Cybercriminals Exploit AI Hype with Deceptive "Noodlophile" Malware Campaign
In the ever-evolving landscape of cyber threats, a new campaign has emerged, exploiting the burgeoning public interest in artificial intelligence. This campaign uses the allure of AI-powered tools to trick unsuspecting users into downloading a malicious information-stealing malware dubbed "Noodlophile." Rather than relying on traditional phishing tactics or compromised software websites, these threat actors have adopted a more sophisticated approach, creating convincing fake AI platforms advertised through seemingly legitimate Facebook groups and viral social media campaigns. This strategy effectively targets individuals seeking AI tools for various creative purposes, such as video and image editing.
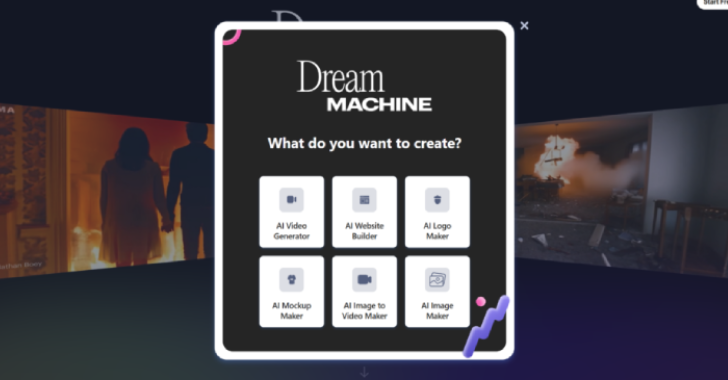
The deceptive campaign employs social media posts that have garnered significant attention, with some exceeding 62,000 views. This high engagement underscores the widespread interest in AI tools and the potential reach of this malicious campaign. Several fake social media pages have been identified, including "Luma Dreammachine Al," "Luma Dreammachine," and "gratistuslibros," all designed to lure users into the trap. These pages advertise links to fictitious AI-powered content creation services, promising the generation of videos, logos, images, and even entire websites. One such fraudulent website mimics the legitimate CapCut AI, an all-in-one video editor, offering users enticing "new AI features."
The unsuspecting user, drawn by the promise of AI-powered content creation, uploads their image or video prompts to these fraudulent websites. They are then prompted to download the supposedly AI-generated content. However, instead of receiving the desired output, they unwittingly download a malicious ZIP archive named "VideoDreamAI.zip." This archive contains a deceptively named executable file, "Video Dream MachineAI.mp4.exe," which initiates the infection chain. The malware cunningly launches a legitimate binary associated with ByteDance’s video editor, "CapCut.exe," using this trusted executable as a cover for its malicious activities.
This legitimate C++-based executable then executes a .NET-based loader, "CapCutLoader," which in turn downloads and executes a Python payload, "srchost.exe," from a remote server. This Python binary serves as the final stage of the infection process, deploying the Noodlophile Stealer malware onto the victim’s system. Noodlophile is designed to harvest a range of sensitive data, including browser credentials, cryptocurrency wallet information, and other valuable user data. In some instances, the stealer is also bundled with a remote access trojan (RAT) like XWorm, providing the attackers with persistent access to the compromised system.
Investigations into the developer of Noodlophile suggest a Vietnamese origin. The individual’s GitHub profile identifies them as a "passionate Malware Developer from Vietnam." The account, created in March 2025, further strengthens the link to Vietnam, a country known for its active cybercrime ecosystem and a history of distributing various stealer malware families targeting Facebook. This recent campaign aligns with previous trends, highlighting the continued exploitation of social media platforms for malware distribution.
The exploitation of public interest in AI technologies for malicious purposes is not a novel tactic. In 2023, Meta reported taking down over 1,000 malicious URLs shared across its platforms, all leveraging the popularity of OpenAI’s ChatGPT as bait to propagate around ten different malware families. This underscores the ongoing trend of cybercriminals capitalizing on emerging technologies to deceive unsuspecting users. The current Noodlophile campaign serves as a stark reminder of the need for vigilance and caution when engaging with online content, particularly those promising access to cutting-edge technologies.
This latest discovery coincides with CYFIRMA’s revelation of another .NET-based stealer malware family, codenamed "PupkinStealer." PupkinStealer, like Noodlophile, is designed to steal a wide range of data from compromised Windows systems, exfiltrating the stolen information to an attacker-controlled Telegram bot. However, unlike Noodlophile’s more complex infection chain utilizing legitimate software, PupkinStealer relies on simpler execution and low-profile behavior to evade detection. Its simplicity makes it an effective, albeit less sophisticated, method of data theft, leveraging common system behaviors and widely used platforms like Telegram for exfiltration. The emergence of both Noodlophile and PupkinStealer underscores the dynamic nature of the cyber threat landscape and the constant evolution of malware tactics. Users must remain vigilant and exercise caution when interacting with online content, especially when dealing with emerging technologies like AI.